Bittium Tough Mobile™  CHighest Level of Security
CHighest Level of Security
Bittium Tough Mobile 2 C is the only true ultra secure encrypted mobile phone on the market that lives up to it’s name. Trusted by many organizations in more than 50 countries, Bittium provides reliable and secure solutions for connectivity, tactical communications for the highest level of security requirements.



Customized for different security needs

Long device lifespan

Unbreakable chain of security
Not Your Average Smartphone
Tough Mobile™ 2C smartphone with DEC Secure ensures privacy where an average smartphone has zero. The average everyday purchased smartphone is built with multiple sensors that have the capabilities of eavesdropping, viewing camera, tracking, and exposing everything about your personal and professional life.
Complete Mobile Security
Bittium Secure Suite enables remote management of devices and applications of the device fleet, protects sensitive data at rest on the smartphone, as well as encrypted IP-based data transfer.
- Dual-boot device with two operating systems and total data separation
- Tamper-proofed to prevent data theft and hardware manipulation
- Non-rootable device firmware
- Disk encryption protected by secure element's authentication and security design
- Trusted boot with hardware and software integrity validation
- Dedicated, tamper-proof secure element for user credentials and encryption keys

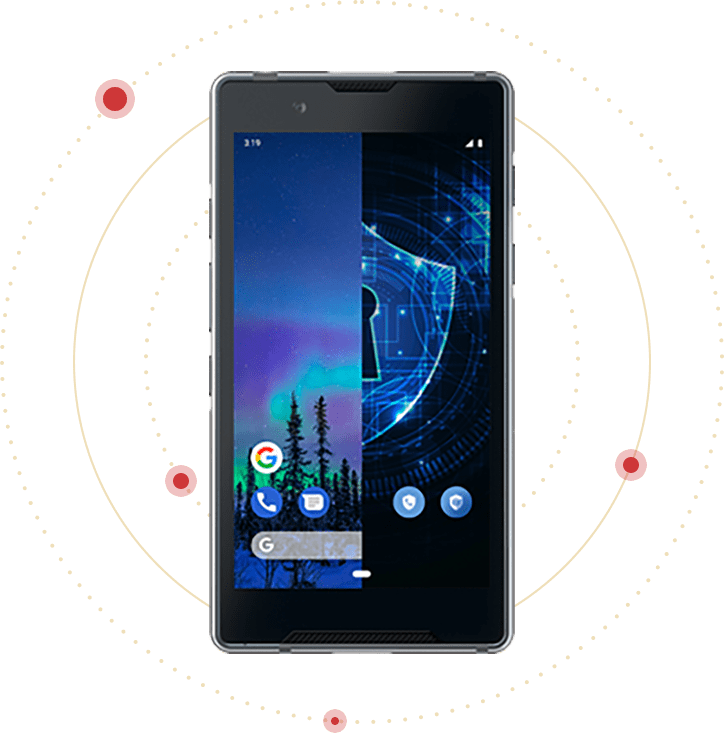
Bittium Tough Mobile 2 C Dual-Boot
Bittium Tough Mobile 2 C always requires Bittium Secure Suite which is an advanced software product with a full set of services for secure communications. This combined solution is available for both private and public organizations and scales up from 10 to thousands of users. It requires installation of a server software, which is provided either as a dedicated IT service or hosted by the customer.
01Next generation tamper detection for preventing data theft and spy
03Hardware-based privacy mode for disabling microphones, cameras, Bluetooth, and reducing sensor sensitivity
05Trusted boot with hardware and software integrity validation
02Designed to be certified for CONFIDENTIAL level
04Device and data in transit secured with Bittium Secure Suite™ device management and encryption software product
06Data secured at all times with multilayered security integrated in hardware and software
07Two separated operating systems
(dual-OS)
- Dual-boot functionality provides two completely separate operating systems with full data separation within one device.
- Confidential use with hardened Bittium Secure OS, allowing demanding authority and use cases
-
 *Yubikey 5 NFC by Yubico included in the sales package
*Yubikey 5 NFC by Yubico included in the sales package
- Personal use with hardened Android 10, where e.g. social media applications are freely available
- User can quickly switch between the two operating systems with dual-boot functionality. Excellent usability and quick two-factor authentication with NFC token* and admin configurable authentication interval.
Several isolated & secure workspaces with Multicontainer feature
Keep your personal and private data separate
Smartphone's unique hardware security solutions and multilayered security structure is based on the hardened Android™ 10 operating system and is reinforced with the dual-boot functionality, running two completely separate and hardened operating systems on a single platform: Confidential and Personal. Both operating systems also support Multicontainer feature, enabling the use of several secure, isolated work spaces within one operating system.
Sensitive Data Secured
Multi-container functionality known as "Secure Zones" enables the use of a single device to manage personal and private data separately and securely.
Easily Accessible
Access workspaces from the home screen and switch between Secure Zones by swiping left or right.
Independent Security
Each Secure Zone has its own security policies for data isolation including independent PIN code protections.
Prevents Data Leakage
Application data and network traffic from the main space and each Secure Zone is securely isolated from each other.
Dedicated Connection
Each Secure Zone has a dedicated and secure VPN connection that all applications within the Secure Zone use.
Multiple Secure Zones
Tough Mobile™ devices can add up to four Secure Zones while generic Androids are limited to a single Secure Zone.
Simultaneous Activity
Secure Zones running in parallel - enables applications from different Secure Zones to be active simultaneously.

Always on VPN
Secure Call will not function if a Secure VPN connection cannot be established, ensuring your communications will never be sent exposed.

Secure & Encrypted Communication
DEC Secure Call delivers everything you expect in a secure communications application including always-on AES-256 encryption; one-on-one and group voice calls, video calls, and messaging. These are the basics.

Limit Google Dependency
The DEC Secure Enterprise App Library provides you access to all of your favorite productivity, finance, communication, and transaction applications you need without ever having to log into Google.
What you get with Bittium DEC Secure for complete mobile security
DEC Secure enables remote management of devices and applications of the device fleet, protects sensitive data at rest on the smartphone, as well as encrypted IPbased data transfer.
Security settings and other parameters of Bittium Tough Mobile 2 C operating systems can be configured with DEC Secure to Restricted, Confidential and beyond. This makes it possible to meet the individual security needs of different organizations, further enhancing the smartphone usability.
This smartphone based solution is certified for CONFIDENTIAL level (NCSA-FI, TL III), and designed to be certified to CONFIDENTIAL level by national security authorities.
- Bittium & DEC Secure
- Configuration of security parameters and other settings
- Audit logs for security related events
- Remote wipe of device
- Remote attestation
- Application whitelisting support
- Bittium SafeMove MDM support
- Bittium SafeMove Mobile VPN to encrypt data in transit
- Hardened password policy
- Multicontainer feature


Your privacy is ensured when green LED blinks
Press and hold button to activate privacy mode
Unique Hardware-Based Privacy Mode
Privacy mode allows simultaneous use of the device, while protecting from:
- Ambient listening by disconnecting microphones from the phone
- Bluetooth sniffing by disabling Bluetooth
- Camera spying by disabling device cameras
- Sensor-based spying by reducing sensor accuracy
Tough Mobile 2 And 2C Compared
| FEATURE | TOUGH MOBILE 2 | TOUGH MOBILE 2C |
| Mobile Device Management | YES | YES |
| Remote Attestation and Log Server | YES | YES |
| Non-Google Option | YES | YES |
| Dual Boot OS | NO | YES |
| Multi Factor Authentication | Optional | Required (YubiKey) |
| Bittium Secure OS | NO | YES |
| Device Segmentation | Multi-Containers | Dual Boot OS |
| Secure Vault | NO | YES |
| DEC Secure VPN | Limited | Always On |
Three Variants
There are currently three different Bittium Tough Mobile 2 variants available, all providing a different level of security.Variants are based on the same hardware, including the security layers built in the device.

Bittium Tough Mobile 2
With Google Mobile Services
For complete end-to-end mobile security, complement the device with Bittium Secure Suite™ device management and encryption software.

Bittium Tough Mobile 2
Without Google Mobile Services
For complete end-to-end mobile security, complement the device with Bittium Secure Suite™ device management and encryption software.

Bittium Tough Mobile 2 C
Two separated operating systems.
Only available for governments and other qualified organizations. Requires Bittium Secure Suite™ device management and encryption software. Certified for CONFIDENTIAL level (NCSA-FI, TL III).
Frequently Asked Questions
General
Does Bittium Tough Mobile 2 C differ from a regular smartphone?
Bittium Tough Mobile 2 C differs from a standard off-the-shelf smartphone as it is designed for secure use.
For example, it has a dedicated secure element storing encryption keys and performing cryptographic operations. The Android based operating system’s security is hardened by Bittium to utilize the dedicated hardware secure element.
It has a mechanical and electrical concept that has been designed to provide a long lifespan for the device. Bittium will also provide software security updates longer than what is usual for regular consumer smartphones.
It has dual-boot functionality, running two completely separate and hardened operating systems on a single platform: Confidential and Personal. This unique dual-boot functionality enables both personal and professional use with high-level information security on a single device, eliminating the need for carrying two separate devices.
The phone also has a unique hardware-based privacy mode for disabling microphones, cameras, Bluetooth, and reducing sensor sensitivity with a touch of a button.
Who can buy the phones and where?
Bittium Tough Mobile 2 C is available for enterprise and government customers. The customers will also need the Bittium Secure Suite server, which is installed in their IT infrastructure. Please contact us for more information.
Where are the phones manufactured?
Tough Mobile 2 C smartphones are designed and manufactured in Finland. Manufacturing is supervised by Bittium and can be audited for certification purposes.
Can Tough Mobile 2 C be used in commercial networks?
Yes, Tough Mobile 2 C can be used in commercial networks as well as in private networks.
In which countries can I use Tough Mobile 2 C?
Tough Mobile 2 C can be used globally and it supports the majority of the used cellular bands. For additional details of the supported bands, please see the supported bands in this website’s Connectivity Highlights section.
What does Tough Mobile 2 C’s “long lifespan” mean?
The phone has a mechanical and electrical concept that has been designed to provide a long lifespan for the device. For example, it has military-grade durability (MIL-STD-810G) and in addition, Bittium provides operating system and software security updates longer than what is usually provided for regular smartphones.
Can I use any Android application with Tough Mobile 2 C?
Yes, Tough Mobile 2 C is verified by Google and it is compatible with all Android applications available for Android 10.
Can Tough Mobile 2 C be customized?
Yes, Tough Mobile 2 C can be customized to meet the security needs of different companies and organizations, further enhancing the smartphone usability. Please contact us for further details.
Can I get Tough Mobile 2 C without Google Mobile Services?
Yes. Although Personal mode operating system always includes Google Mobile Services, with Bittium Secure Suite it is possible to disable the Personal mode, leaving only Bittium Secure operating system without Google Mobile Services in use.
When using Tough Mobile 2 C without Google Mobile Services and Google Play, am i able to install applications?
With Bittium Secure Suite software product and its back-end server you can install approved Android applications through the Application Library.
Can I receive further details about mobile security and specific product features?
All publicly available product information is on our website. More detailed technical information, training and dedicated customer support is available for B2B customers under Non-Disclosure-Agreement (NDA).
What is the difference between the two operating systems in Tough Mobile 2 C?
Operating system in the Confidential mode is completely separated and hardened for secure use, and it’s intended for ultimate, government-level secure communications.
Hardened Android operating system in the Personal mode is for personal use where e.g. Google services and other social media applications are freely available.
This unique dual-boot functionality enables both personal and professional use with high-level information security on a single device, eliminating the need for carrying two separate devices. The user can switch between the two different modes with dual-boot functionality.
What does Tough Mobile 2 C sales box include?
Bittium Tough Mobile 2 C sales box include: Embedded 3000mAh Li-Ion battery, Charger with EU or UK plug, USB-C cable, Stereo headset, SIM tray tool, User guide, Secure Suite and NFC Dongle.
How long will the security updates be available?
Bittium Tough Mobile 2 C is guaranteed to have a long life cycle and support for security updates. Android 11 version update is under planning. Device security updates will be available minimum until year 2024.
Security
What does 'highest level for security' mean?
Highest level of security means that the device has been designed to meet even the highest governmental grade security requirements.
Tough Mobile 2 C has been designed for ultra secure use, starting from tamper-proofed mechanics to always-on security monitoring of electronics and hardened software solutions utilizing the Android 9 operating system.
Security is always based on hardware originated tamper proof security solutions.
Smartphone’s unique HW security solutions and multilayered security structure are reinforced with the dual-boot functionality, running two completely separate and hardened operating systems on a single platform: Confidential and Personal.
Bittium highest security also means that the device has been designed and manufactured by a trusted vendor in Finland.
What does Tough Mobile 2 C’s “multilayered security” mean?
Tough Mobile 2 C’s security is built in layers, both in hardware and software.
The security built in the hardware protects data at rest. Security starts from the design and manufacturing of the device, including a hardware secure element that for example stores all authentication data and encryption keys. For software-based security Tough Mobile 2 C always comes with Bittium Secure Suite™ full set of services for securing the data in transit.
What does Tough Mobile 2 C’s dedicated hardware secure element do?
The hardware secure element provides for example user authentication services for Android, stores device encryption keys and provides cryptographic operations. If the Android OS becomes compromised with malware with access to everything, it still would not be able to access the contents of the secure element.
Secure element also controls the tamper detection feature of the device – even if the device’s main battery has run out. The secure element is powered by its own backup battery.
How is data in Tough Mobile 2 C encrypted?
All data in Tough Mobile 2 C is encrypted with AES-256 encryption. Tough Mobile 2 C supports also encryption for data in SD cards. Data in transit is encrypted with Bittium SafeMove® Mobile VPN included in Bittium Secure Suite.
How is Tough Mobile 2 C tamper-proofed?
Tough Mobile 2 C’s secure element detects if someone is trying to for example drill, open, disassemble, or precision cut the device. If tampering is detected, the secure element cryptographically erases all data from the device, even if the main battery has ran out of power. The secure element is powered by its own rechargeable backup battery.
How is Tough Mobile 2 C protected from unwanted hardware implants?
Tough Mobile 2 C is tamper-proofed, which means that the phone detects if it is dismantled or the SIM slot is opened. For security reasons all data is cryptographically erased in case of dismantling. When the SIM slot is opened, device locks instantly and only the device’s original user can dismiss notification of SIM slot opening by authenticating to the device and continue using the device.
How is Tough Mobile 2 C protected from malicious firmware?
Tough Mobile 2 C can be used only with Bittium signed firmware delivered by Bittium. Device utilizes secure/trusted boot, OS rollback prevention and the device is non-rootable. In each start up the device checks firmware and hardware integrity. For additional security layer, Bittium Secure Suite can be used to remotely attest the device firmware and hardware.
What does Bittium Secure Suite provide and how can I take it into use with Tough Mobile 2 C?
Bittium Secure Suite is an advanced software product that complements Bittium Tough Mobile 2 C with a full set of services for secure communications, including MDM, VPN, remote attestation and application whitelisting. It is available for both private and public organizations, and requires installation of a back-end server, which is provided either as a dedicated IT service or hosted by the customer.
Is VPN included with Tough Mobile 2 C?
Tough Mobile 2 C is always complemented with Bittium Secure Suite software which has Bittium SafeMove® Mobile VPN client software pre-installed to secure data in transit. Please contact us for more information and for starting a Bittium Secure Suite trial.
Tough Mobile 2 C device supports also any 3rd party VPN solutions supported by Android 9.
What does the Multicontainer solution do?
Both operating systems support Multicontainer feature, enabling the use of several secure, isolated workspaces within one operating system, preventing data contamination between applications/services located in container workspaces. With Multicontainer, it is possible to use classified data and services from several separate organizations as each container workspace isolates applications, data and network traffic from all other workspace containers.
User can switch between the different workspaces by swiping sideways from the home screen.
Services within the workspaces are protected and managed with Bittium Secure Suite. Services in workspace containers can connect to isolated back-ends via container-specific VPN tunnels, providing unique data-in-transit protection for each workspace.
How can I enable the Multicontainer solution?
Multicontainer solution is enabled with the Bittium Secure Suite back-end system as each container uses its own VPN tunnel and server environment for isolating and encrypting data in transit. Please contact us to get the complete solution for your organization.
How can I create a single container in Tough Mobile 2 C?
Multicontainer solution is enabled and controlled with Bittium Secure Suite back-end system.
What does the hardware-based Privacy Mode mean and how does it work?
With Privacy Mode the user can prevent eavesdropping and spying through device by disabling microphones, Bluetooth, cameras and reducing sensor accuracy on the device at the hardware-level. Privacy Mode can be activated/deactivated by pressing and holding the privacy button, which is the topmost button on the right-hand side of the phone. A green indicator light starts blinking on the front side of the phone when Privacy Mode is active.
How can I make encrypted calls with Tough Mobile 2 C?
Making encrypted calls is possible with dedicated secure voice applications, which are available from Bittium and its solution partners. Please contact us for more information.
How is Tough Mobile 2 C’s operating system hardened?
For example, Tough Mobile 2 C’s security/encryption key management, user authentication and true random number generation are moved from Android to Bittium hardware-based secure element. If you would like to discuss what additional hardenings have been made, please contact us.
How can I quickly erase all my data from the phone in emergency situations?
Tough Mobile 2 C is provided with a Fast Wipe functionality to erase all data in emergency situations. User can trigger Fast Wipe from drop-down menu by pressing the red Fast Wipe icon and giving the device PIN.
How do I get security updates to Tough Mobile 2 C?
All Tough Mobile 2 C updates are delivered Over-The-Air (OTA).
Bittium Secure Suite allows full control over which devices are updated, when, and with which firmware. The OTA delivery can also be protected by VPN. Bittium can also provide its customers with professional service tools for local updates.
Can Tough Mobile 2 C be security certified for national security purposes?
Yes, Tough Mobile 2 C has been designed to be certified for national security purposes. CONFIDENTIAL level approvals are in progress. Device and manufacturing audits are possible for certification purposes.
Technical
How can I activate the Emergency button?
Use of the emergency button requires a separate application providing the functionality. When the suitable application supporting Bittium emergency button has been installed, go to Settings → Buttons → Emergency Button Function and select Emergency application from the list.
How can I activate the Push-To-Talk button?
Use of the PTT/PTV button requires a separate application providing the functionality. When the suitable application supporting Bittium PTT button has been installed, go to Settings → Buttons → PTT Button Function and select PTT application from the list.
What does “MIL-STD-810G” mean?
MIL-STD-810G is a US military standard that defines a broad set of environmental (such as shock, vibration, temperature, humidity) requirements for mobile devices that are designed for use in harsh environments. Tough Mobile 2 C has been tested against the MIL-STD-810G shock and drop standards.
What does “IP67 water and dust resistant” mean?
IP67 level water and dust resistant means that the device is built to be protected from dust and is operational after being submerged in 1 meter of water for 30 minutes. IP67 does not mean that device is designed to be used underwater.
Does the device support dual-SIM functionality?
Yes, Tough Mobile 2 C supports Dual SIM Dual Standby and has dual nano-SIM slots.
Can the internal memory/storage be expanded?
Yes, Tough Mobile 2 C has a combined nano-SIM/MicroSD expansion slot which can be used to provide up to 256GB of additional memory/storage.
Does the device support external keyboard and display?
Yes, Tough Mobile 2 C supports external keyboards and displays via its USB-C connector in Personal mode only.
How can I take screenshots with Tough Mobile 2 C?
You can take screenshots by pressing and holding the Power button until pop-up menu appears. From pop-up menu select “Screenshot”. If containers are enabled, taking screenshots is disabled by default.
What is the battery size/life for the device?
Tough Mobile 2 C has a 3000mAh embedded battery. Due to the device’s highly optimized power management, it will provide up to 460h standby time and up to 20h talk times. Actual results may vary depending on usage and environmental factors.
To make your battery last longer, you have multiple options.
Turn off tethering and hotspots when you’re not using them, go to Settings -> Network & Internet -> Hotspot & tethering -> Wi-Fi hotspot.
Turn off your Wi-Fi and Wi-Fi scanning when you are not using them, go to Settings -> Network & Internet -> Wi-Fi.
Turn off your Bluetooth when you are not using it, go to Settings -> Connected devices -> Connection preferences -> Bluetooth.
Turn off location when it is not necessary, go to Settings -> Security & location -> Location. Note that some applications and features don’t work without location services.
Turn off Google apps automatic downloads and updates;
go to Google Play -> Settings -> App download preference -> Ask me every time.
go to Google Play -> Settings -> Auto-Update apps -> Don’t auto-update apps.
Which charger plugs are provided with the phone?
Bittium can provide Tough Mobile 2 C with either EU, UK or US charger plugs.
How can I activate the Recovery mode?
Make sure the device is powered off.
Press ‘volume up’ button and keep it pressed -> press the ‘power’ button shortly and release it.
You should now enter the screen where you see an Android robot icon and text ‘no command’.
-> Release ‘volume up’ key -> press the ‘power’ key, keep it pressed and press shortly ‘volume up’ key -> release ‘power’ key.
You should now enter the recovery menu where you can perform a factory reset. Use volume up and down keys for navigation, ‘power’ key for menu item selection.
Note: If ‘power’ key is pressed over 10s, the phone will automatically restart. Start over from the beginning if this happens.
Support
How long is the product warranty?
Product warranty for Bittium Tough Mobile 2 C is one (1) year, including all accessories provided in the sales box, against defects in materials or workmanship. If the device is found to be defective within the one year warranty period, Bittium will repair or replace it with a new or refurbished device, at its option, at no charge to the customer, except as set forth below.
This warranty does not cover cosmetic damage, or device failure caused by liquid damages, or damage due to misuse, abuse, negligence, accident, modification or disassembly of any part of the device. The warranty does not cover damage due to improper operation or maintenance, connection to improper voltage supply, or attempted repair by anyone other than a facility authorized by Bittium to service this Tough Mobile 2 C.
Can the product warranty be extended?
Yes, private and public organizations can purchase Extended Warranty for additional 12-36 months. Please contact us for more information.
How do I update the software on my Tough Mobile 2 C?
All Tough Mobile 2 C updates are delivered Over-The-Air (OTA).
Bittium Secure Suite allows full control over which devices are updated, when and with which firmware. The OTA delivery can also be protected by VPN. Bittium can also provide its customers with professional service tools for local updates.
How can I change the battery?
Bittium offers a replacement service if there is a need to replace the battery. Distributors and partners, please visit the Bittium Tough Mobile Support Portal for Partners to submit service requests. If you do not have an account for the Support Portal, please fill the Bittium Tough Mobile Support Request Form to make your service request.
Who can I contact for product support and maintenance?
Please first read through all the FAQ and Support information on the Tough Mobile 2 C webpage.
If your problem is not solved, distributors and partners please visit the Bittium Tough Mobile Support Portal for Partners to submit error reports, support requests, service requests, and feature requests. If you don’t have an account for the Support Portal, please fill the Bittium Tough Mobile Support Request Form to make your support request.
Spy Emporium Reviews
Maria Rodrieguez 2 Years ago
Charlotte Gladders 2 Years ago
nathan O'grady 2 Years ago

Free Delivery Free Delivery over $50

Secure Payment Encrypted Secure Checkout

Discreet Discreet Billing & Shipping

Returns Easy Return Policy
Explore Categories
- Body Worn Cameras
- Camera Accessories & Add-ons
- Brackets & Housings
- Cables
- Camera Lens
- Connections
- Converters
- Input Devices
- IR Illuminatiors
- Hard Drives & Memory Cards
- Power Boxes
- Power Supplies & Batteries
- Security Signs & Stickers
- Tools & Testers
- Lock Boxes
- CCTV Cameras
- Cameras integrated with Screens
- Covert Cameras
- Micro Cameras
- PTZ Cameras
- Dome Cameras
- Bullet Cameras
- Box Cameras
- Fake Dummy Cameras
- IP Cameras
- Covert Wi-Fi Cameras
- Door Cameras
- Hidden Cameras Recording to SD
- On The Go Spy Cams
- Vehicle Cameras
- Wi-Fi Security Cameras
- 4G LTE Cellular Mobile Spy Cameras